
Cybercrime- the fastest growing criminal activity
If you're concerned about the constant flow of outrageous breaking news reports about cybercrime, we are too. As the fastest-growing criminal activity in the U.S., cybercrime is wreaking havoc by maliciously disabling and damaging computers, breaching systems to mine personal data, gaining unauthorized access to networks, and even disrupting global production.
Cybercriminals have recently shifted towards the profitable reward of bigger payouts by targeting businesses. But individual consumers should actively work to protect their personal and professional information to prevent being hacked. The FBI reported a 400% spike in reported cybercrimes to their Internet Crime Complaint Center (IC3) since the beginning of the COVID pandemic. The dramatic shift to a highly remote workplace and heavy reliance on the internet for important information and services provided a unique opportunity for cybercrime.

The Two Biggest Hacking Threats
Phishing and ransomware are now the most preferred methods of data theft. While it's become a serious risk to business production and services, the threats are still very real for consumers. Let's talk about how these prominent types of cyberattacks happen and best practices to protect you and your family.
Ransomware
Ransomware is a form of malware designed to extort money by threatening to cause extensive damage to your data or perpetually block access to it unless a ransom is paid. This malware program holds your computer hostage and demands payment to get a decryption key that gives access back to you.
Your computer picks up ransomware through phishing emails with links or attachments or drive-by downloading. Drive-by downloading can happen when you visit an infected website and malware is downloaded and installed without your knowledge. There are other varieties of ransomware that spread through social media and instant messaging applications.
Phishing
In a phishing scheme, you are tricked by email or text into providing valuable information like passwords to accounts, credit card details, and intellectual property. The fake correspondence disguised as your bank, credit card company, or tax department provides a link and asks you to do something, like reset a password or make an account change. There's often a sense of urgency or a claim that your account is in danger.
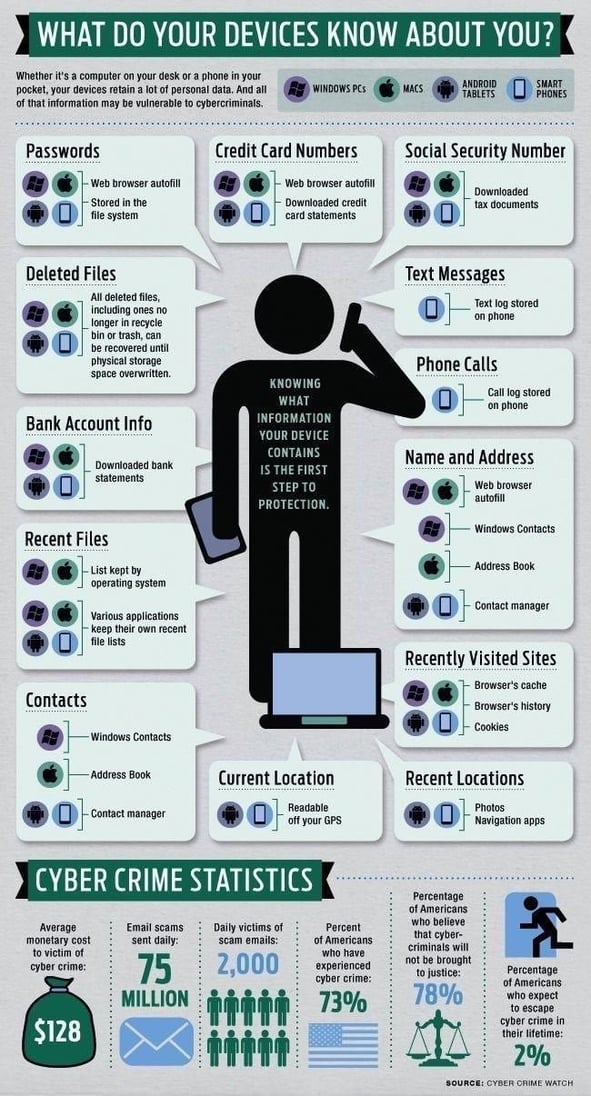
How to prevent cybercrime at home
Consider how much of your personal information is at risk. Your device tracks each online account, every transaction you make, and sensitive data with every keystroke and download. You also most likely have all your pictures and other valuable content at risk. The following six smart practices, you can prevent an attack and protect yourself against expensive damage and heartbreaking loss.
6 Ways to prevent a home cyber attack
1. Update, Update, Update
Most people don't update their systems unless they are experiencing a problem. But an outdated computer or device is like a home without door locks. Whether it's Windows on your PC or IOS on your phone, keeping up with the freshest update is not only good for bug fixes and compatibility issues, but it's critical to reducing your software vulnerabilities from the most recent security threats. You can even schedule automatic updates in your settings, so you don't have to remember to keep up with it.
2. Create Complicated Passwords
Using complex passwords unique to each device and account is extremely important to securing your data. And change them regularly. Using a password manager is an easy way to protect all your access points.
If you don't opt for a password manager and want to create and manage passwords yourself, be sure to use long passwords with upper and lower case letters and other unique characters.
Here are some other good password features:
- The longer, the better: 12 characters or more.
- Base it on random things, not personal information.
- Use numbers and special characters.
- Avoid sequences like "4567".
- Skip reusing old passwords.
- Use a passphrase that's easier to remember and replaces letters with characters or numbers: "The pig's name is Fred": tH3P1g$n@me1sFr3d

3. Watch Those Links
Phishing schemes often involve emails or texts with malicious links that are not what they seem. They disguise themselves as an organization you have an account with, like your bank, an online payment website or app, a credit card company, social networking site, or an online store. They even steal logos and may appear like the real thing. Here's what to look for:
- Observe the sender's email address. Does anything look out of place or misspelled?
- On a PC, hover your mouse over the link but DO NOT click. Look at the link's true destination — usually in the status line at the lower left-hand side of your screen or program window. Try it now. Hover over the link: www.ebay.com and you will see "http://buyleoalatte.com".
- On a cell phone or other device, press and HOLD the link (long-press) to see a preview of the URL without visiting it.
- Is there a sense of urgency in the messaging? Red flag! This is a tactic used to get you to act quickly without taking time to think about it.
- What information is requested? Legitimate organizations and account holders do not ask you for personal information in an email or text.
- Contact the business or account holder directly using phone or website contact information you know is real and ask if they contacted you.
4. Use Multi-factor Authentication
More and more vendors of accounts offer multi-factor authentication. If they do, use it. The process provides another layer of protection by requiring two or more credentials to log in, like a code or authentication app.
5. Back-up Your Data
It's always a good idea to back up your computer files to the cloud or an external hard drive that is not connected to your network. A data backup is a copy of the important information stored on your devices and can be used to restore it after a ransomware attack, device failure, or theft. You can purchase an external hard drive for less than $100. It should be disconnected from your network when not in use.
6. Consider Cyber Insurance
Cyber coverage is becoming a valuable part of an insurance portfolio. It protects your assets by providing coverage for identity theft expenses, cyber extortion costs, and data leaks, plus credit card fraud, forgery, and wire transfer fraud.

What do to if you think you were hacked
If you clicked on a link or opened an attachment, here's how to take action immediately:
- If it's a work account or device, report it to your IT Team immediately.
- Disconnect the infected device from your network to prevent spread.
- Update your computer's security software and system software.
- Run a virus scan.
- If you think your personal data was hacked, visit IdentityTheft.gov and take specific steps based on your lost information.
- Contact banks, credit card companies, and any other account holder involved.
- Consider freezing your credit unless you have previously done so.
- Report it to the FBI Internet Crime Complaint Center.
- Check to see if your email and password have been involved in a data breach with a company where you have an account. Go to the website haveibeenpwned.com. You can also set up notifications to let you know if it happens in the future.
Learn more about Cyber Protection Coverage with a NNINS Home Insurance policy
Learn more about homeowners insurance in Virginia >
THE NORTHERN NECK INSURANCE INTEGRITY PROMISE — We pledge to provide straight talk and good counsel from our NNINS Virginia insurance experts through our blog. While we hope you find this to be a helpful source of information, it does not replace the guidance of a licensed insurance professional, nor does it modify the terms of your Northern Neck Insurance policy in any way. All insurance products are governed by the terms in the applicable insurance policy.




